The scariest sites on the Net? They’re not the ones you might suspect. Here’s what to watch for and how to stay safe.
By Nick Mediati
PC World
Those photos of Jessica Alba may be murder on your PC. That Google search result that looks as if it answers all your questions may do nothing but create a serious tech headache. The fun you had watching that hilarious video you downloaded may not be worth the misery it can cause your system.
You’ve been warned that the Internet is something of a security minefield–that it’s easy to get in trouble. You can do everything you can think of to protect yourself and still be taken by a malware infection, a phishing scam, or an invasion of online privacy. We’d like to provide a little help. Here are some of the hazards you may encounter, how dangerous they are, and what you can do to stay out of harm’s way.

Not all Web dangers are created equal. Thankfully, our friends at the Department of Homeland Security have made our work of classifying Web threats a little easier. Will you get taken just by visiting that unfamiliar site? Or will you have to look for trouble? Let our threat level indicator be your guide.

Threat 1 >> Malicious Flash files that can infect your PC
The Place: Websites that use Flash
 Adobe’s Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser’s cookies, Flash cookies get left behind.
Adobe’s Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser’s cookies, Flash cookies get left behind.
If You Have to Go There: To help protect against Flash-based attacks, make sure you keep your Flash browser plug-ins up-to-date. And you can configure the Flash plug-in to ask you before it downloads any Flash cookies.
Threat 2 >> Shortened links that lead you to potentially harmful places
The Place: Twitter
 Scammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.
Scammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.
And it’s very simple to hide malware or scams behind shortened URLs. A shortened link that supposedly points to the latest Internet trend-du-jour may be a Trojan horse in disguise.
If You Have to Go There: Simply don’t click links. Of course, that takes some of the fun out of Twitter. The other option is to use a Twitter client app. TweetDeck and Tweetie for Mac have preview features that let you see the full URL before you go to the site in question.
Some link-shortening services, such as Bit.ly, attempt to filter out malicious links, but it seems to be a manual process, not an automatic one. TinyURL has a preview service you can turn on.
Threat 3 >> E-mail scams or attachments that get you to install malware or give up personal info
The Place: Your e-mail inbox
 Although phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they’re becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something’s amiss is the sender’s e-mail address.
Although phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they’re becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something’s amiss is the sender’s e-mail address.
If You Have to Go There: Don’t trust anything in your inbox. Instead of clicking on links in a retailer’s e-mail, go directly to the retailer’s site.
Threat 4 >> Malware hiding in video, music, or software downloads
The Place: Torrent sites
 Torrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files–they may be malware in disguise.
Torrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files–they may be malware in disguise.
Ben Edelman, privacy researcher and assistant professor at Harvard Business School, thinks torrent sites are the most dangerous places to visit, since they don’t have a business model or reputation to defend (by comparison, many porn sites rely on being deemed trustworthy). “The [torrent] customers, they really don’t want to pay,” he says.
If You Have to Go There: It’s probably best to avoid torrent sites entirely, given their untrustworthy content, but if you must visit, use a secondary PC to protect your main system. Use antivirus software, and keep it updated. Scan downloaded files and wait a couple of days before opening them. Brand-new malware can be tricky to catch, but the delay in opening may allow your antivirus software to get the necessary signatures.
Threat 5 >> Malware in photos or videos of scantily clad women
The Place: ‘Legitimate’ porn sites
 Porn sites have a reputation of being less secure than mainstream sites, but that assumption doesn’t tell the whole story. “There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it’s a given that you’ll be attacked at some point,” says Roger Thompson, chief research officer with security firm AVG. “Unfortunately, staying away from those sites won’t keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers.”
Porn sites have a reputation of being less secure than mainstream sites, but that assumption doesn’t tell the whole story. “There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it’s a given that you’ll be attacked at some point,” says Roger Thompson, chief research officer with security firm AVG. “Unfortunately, staying away from those sites won’t keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers.”
And as mentioned earlier, many porn sites operate as actual, legitimate businesses that want to attract and retain customers. That said, it may be hard to tell the “legit” porn sites from malware-hosting sites that use porn as a lure.
If You Have to Go There: Be suspicious of video downloads, or sites that require you to install video codecs to view videos (see the next threat, below). Using tools like AVG’s LinkScanner and McAfee’s SiteAdvisor (or SiteAdvisor for Firefox) can help you weed out the malicious sites.
And, again, consider visiting such sites on a secondary machine. You don’t want your browser history on the family PC.
Threat 6 >> Trojan horses disguised as video codecs, infecting your PC with malware
The Place: Video download sites, peer-to-peer networks
 If you watch or download video online, you’ve likely been told to download a video codec–a small piece of software that provides support for a type of video file–at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.
If you watch or download video online, you’ve likely been told to download a video codec–a small piece of software that provides support for a type of video file–at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.
If You Have to Go There: Your safest option is to stick with well-known video sites such as YouTube and Vimeo. And for catching up on the latest episodes of your favorite TV shows, sites and services like Hulu, TV.com, ABC.com, and iTunes are safer than peer-to-peer networks.
Threat 7 >> Geolocation–your smartphone and perhaps other parties know where you are
The Place: Your smartphone
 The smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use–or abuse–of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called pleaserobme.com showed that–for a time–a stream of FourSquare check-ins indicated that a person was away from their home (the site’s goal, mind you, wasn’t to condone theft, but to raise awareness of the issue).
The smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use–or abuse–of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called pleaserobme.com showed that–for a time–a stream of FourSquare check-ins indicated that a person was away from their home (the site’s goal, mind you, wasn’t to condone theft, but to raise awareness of the issue).
![]()
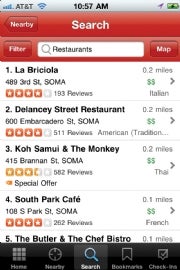 As in this example showing restaurants in a San Francisco neighborhood, some smartphone apps, such as Yelp for iPhone, use your physical location to provide you with information on nearby businesses or points of interest.Apple recently updated its privacy policy to reflect changes in how it handles location data in iOS 4. The policy now states that “to provide location-based services on Apple products, Apple and our partners and licensees may collect, use and share precise location data.” You can read more on Apple’s new privacy terms and what they mean for you.
As in this example showing restaurants in a San Francisco neighborhood, some smartphone apps, such as Yelp for iPhone, use your physical location to provide you with information on nearby businesses or points of interest.Apple recently updated its privacy policy to reflect changes in how it handles location data in iOS 4. The policy now states that “to provide location-based services on Apple products, Apple and our partners and licensees may collect, use and share precise location data.” You can read more on Apple’s new privacy terms and what they mean for you.
If You Have to Go There: Be particular about the location-based sites, apps, and services that you use. As shown in the screenshot at right services such as Yelp provide good examples of useful location-aware apps. On the other hand, weigh the privacy implications of services like FourSquare or the new Facebook Places feature, and consider how much you feel comfortable divulging. (Read more on how to retain privacy on FourSquare and Facebook Places.)
Threat 8 >> ‘Poisoned’ search engine results that go to malware-carrying Websites
The Place: Search engines
 Search engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for “Cameron Diaz and screensavers” had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.
Search engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for “Cameron Diaz and screensavers” had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.
If You Have to Go There: Pick and choose which sites to go to. Don’t just blindly click search results; check each URL first to make sure that it really leads to the site you want. Although any site can be hacked, visiting the Washington Post’s story on a hot news topic, for example, is probably a wiser choice than following a link to a site you’ve never heard of before.
Threat 9 >> Malicious PDFs that try to fool you into installing malware
The Place: Hacked Websites, plus your inbox
 As Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in Adobe Acrobat is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in Adobe Reader and Adobe Acrobat; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.
As Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in Adobe Acrobat is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in Adobe Reader and Adobe Acrobat; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.
![]()
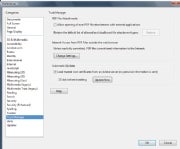 Feeling particularly paranoid? Uncheck ‘Allow opening of non-PDF file attachments with external applications’ (near the top) to head off certain PDF exploits.A newer variant takes an otherwise innocent-looking PDF document and inserts malware into it. Adobe Reader may pop up an alert asking if you want to run the malware, but hackers can edit those messages to trick you into opening the file.
Feeling particularly paranoid? Uncheck ‘Allow opening of non-PDF file attachments with external applications’ (near the top) to head off certain PDF exploits.A newer variant takes an otherwise innocent-looking PDF document and inserts malware into it. Adobe Reader may pop up an alert asking if you want to run the malware, but hackers can edit those messages to trick you into opening the file.
How serious is this problem? In 2009, attacks using malicious PDFs made up 49 percent of Web-based attacks, according to security firm Symantec.
If You Have to Go There: First, always make sure that you’re running the latest version of Adobe Reader.
You can also use a different PDF reader, such as Foxit Reader. This can protect you from attacks on holes in Adobe Reader itself, but it won’t make you immune to all PDF attacks, such as the newer ones that embed malware inside the PDFs. Make sure, also, that you update to Adobe Reader 9.3.3 or later (Reader 8 users should update to version 8.3.3 or later); these updates change the way Adobe Reader handles non-PDF attachments and reduce the risk from such attacks.
You can turn off Adobe Reader’s ability to open non-PDF attachments by going to Preferences, clicking Trust Manager, and unchecking Allow opening of non-PDF file attachments with external applications.
The next major release of Acrobat and Reader will provide a new “protected mode” against these attacks.
Threat 10 >> Malicious video files using flaws in player software to hijack PCs
The Place: Video download sites
 Attackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often “malformed” video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.
Attackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often “malformed” video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.
If You Have to Go There: Keep your player software up-to-date. Apple and Microsoft periodically release patches for QuickTime and Windows Media Player, respectively. Avoid downloading videos at random. Stick to well-known video sites such as YouTube, or to download services like iTunes.
Threat 11 >> Drive-by downloads that install malware when you visit a site
The Place: Hacked legitimate sites
 A drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.
A drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.
If You Have to Go There: The first thing to do is to keep your security software up-to-date, and to run regular malware scans. Many security suites can flag suspicious downloads.
Threat 12 >> Fake antivirus software that extorts money–and your credit card information
The Place: Your inbox, hacked legitimate sites
 Fake antivirus programs look and act like the real thing, complete with alert messages. It isn’t until you realize that these alerts are often riddled with typos that you know you’re in trouble.
Fake antivirus programs look and act like the real thing, complete with alert messages. It isn’t until you realize that these alerts are often riddled with typos that you know you’re in trouble.
Most fake antivirus software is best described as extortionware: The trial version will nag you until you purchase the fake antivirus software-which usually does nothing to protect your PC. Once you send the criminals your credit card information, they can reuse it for other purposes, such as buying a high-priced item under your name.
You can get infected with a fake antivirus app in any number of ways. For example, in drive-by downloads (see the previous item), a malicious payload downloads and installs without the user realizing it or having any time to react.
If You Have to Go There: If you get an alert saying you’re infected with malware, but it didn’t come from the antivirus software you knowingly installed, stop what you’re doing. Try booting into Safe Mode and running a scan using your legitimate antivirus software.
However, such a scan may not clean up all of the malware-either the scanner doesn’t have a signature for one fragment, or that piece doesn’t act like traditional malware. This may render behavioral detection (which spots malware based on how it acts on your system) useless. If all else fails, you may need to call in a professional.
Threat 13 >> Fraudulent ads on sites that lead you to scams or malware
The Place: Just about any ad-supported Website
 Hey–ads aren’t all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google’s Sponsored Links ad program and placing ads that looked like links to major companies’ Websites.
Hey–ads aren’t all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google’s Sponsored Links ad program and placing ads that looked like links to major companies’ Websites.
“The bad guys have become very clever at exploiting online advertising networks, tricking them into distributing ads that effectively load malicious content–especially nasty, scaremongering pop-ups for rogue antispyware,” says Eric Howes, director of research services for security firm GFI Software.
If You Have to Go There: Most large sites, such as PCWorld.com, have ad sales departments that work frequently with a core group of large advertisers, so it’s probably safe to click a Microsoft ad on the New York Times site. But as the Google Sponsored Links incident shows, nothing is entirely fail-safe.
Threat 14 >> Questionable Facebook apps
The Place: Facebook
 Facebook apps have long been an issue for security experts. You don’t always know who’s developing the apps, what they’re doing with the data they may be collecting, or the developers’ data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer’s hands.
Facebook apps have long been an issue for security experts. You don’t always know who’s developing the apps, what they’re doing with the data they may be collecting, or the developers’ data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer’s hands.
![]()
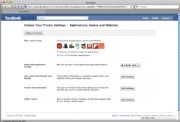 Take a few minutes to check your Facebook application settings to make sure that your app privacy settings are as you want them.If You Have to Go There: Be selective about the apps you add to your profile–don’t take every quiz, for example. Check your privacy settings for Facebook apps, as well: Click the Account drop-down menu in the upper-right corner of Facebook’s site, select Privacy Settings, and then click Edit your settings under ‘Applications and Websites’. There, you can control which apps have access to your data, and which of your friends can see what information from apps (such as quiz results); you can also turn off Facebook apps altogether.
Take a few minutes to check your Facebook application settings to make sure that your app privacy settings are as you want them.If You Have to Go There: Be selective about the apps you add to your profile–don’t take every quiz, for example. Check your privacy settings for Facebook apps, as well: Click the Account drop-down menu in the upper-right corner of Facebook’s site, select Privacy Settings, and then click Edit your settings under ‘Applications and Websites’. There, you can control which apps have access to your data, and which of your friends can see what information from apps (such as quiz results); you can also turn off Facebook apps altogether.
Threat 15 >> Sites that lure you in, get you to sign up, then sell your e-mail address for spam
The Place: ‘Free electronics’ sites
 You’ve no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It’s easy! These sites aren’t typically dangerous in the classical sense–you probably won’t get infected with malware–but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.
You’ve no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It’s easy! These sites aren’t typically dangerous in the classical sense–you probably won’t get infected with malware–but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.
If You Have to Go There: Read the privacy policies. And then read them again. Also, beware of privacy policy loopholes–even though a site says that it won’t sell your private data to third parties, depending on the language of the policy, they may still be able to give your information to “affiliates.”
Threat 16 >> Phishing 2.0 on social networks that tricks you into downloading malware or giving your Facebook login information to a criminal
The Place: Social networks
 Questionable Facebook apps and malicious shortened links aren’t the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person’s Facebook account, then use it to lure that person’s friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information–thereby giving scammers one more Facebook account to hijack.
Questionable Facebook apps and malicious shortened links aren’t the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person’s Facebook account, then use it to lure that person’s friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information–thereby giving scammers one more Facebook account to hijack.
“One of the bigger dangers currently facing users is malware, adware, and spyware spread through social networks like Facebook and Twitter,” says Eric Howes, director of malware research with Sunbelt Software. “Users may receive spam via these networks offering them free deals, links to interesting videos, or even widgets to enhance their Facebook profiles. In many cases what’s really being pushed on users is adware, spyware, or even malicious software that can exploit users’ PCs.”
If You Have to Go There: Don’t trust every link posted to Facebook, even if one of your friends posted it. Be especially suspicious if the post is out of the ordinary for that person. Check the person’s wall or Twitter @-replies to see if anyone is concerned that the person’s account has been compromised.
And if you suspect that your account has been hijacked, change your password immediately. Both Facebook and Twitter have resources to help you keep up-to-date on the latest threats on both sites. Facebook users should visit its security page; if you’re on Twitter, be sure to follow @spam and @safety for Twitter security best practices.
Threat 17 >> Oversharing–exposing too much personal information on your social network profiles
The Place: Social networks
 How many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn’t just a matter of getting a little too personal–it can leave your private information viewable to the general public. But it’s avoidable.
How many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn’t just a matter of getting a little too personal–it can leave your private information viewable to the general public. But it’s avoidable.
“There is a subtle danger that few people understand with the social networking sites, and that is the idea of information leakage,” says AVG’s Roger Thompson. “People, particularly teens, put all sorts of information online, without realizing that many more people than just their friends can see that data.”
Oversharing could very well lead to more serious privacy issues further down the road, Thompson adds. “As today’s young teens reach an age to apply for a credit card, I fully expect an onslaught of fraudulent card applications on their behalf, because they unwittingly divulged so much information. Harvesting is going on now, and we have no idea who is doing the harvesting.”
If You Have to Go There: This particular threat is relatively easy to avoid, in that a little common sense can go a long way: Just be mindful of what you post. Do you really need to publish your home address and phone number to your Facebook profile?
Finally, be certain to check your privacy settings to make sure that you’re not divulging your deepest, darkest secrets to all 500 million Facebook users.













A very informative article…thanks for posting!
hacking has a new face! I think 14 and 16 are particularly relevant for FB users…
Hi, I check your blog on a regular basis. Your story-telling style is witty, keep it up!|
Your interest is contagious as well as your hard work and devotion have been indispensable. We can’t thanks enough for whatever that you do!
Thanks for your post. I would also love to say that the health insurance brokerage also utilizes the benefit of the coordinators of the group insurance policy. The health insurance agent is given an index of benefits needed by somebody or a group coordinator. What a broker can is look for individuals or even coordinators which will best complement those desires. Then he reveals his suggestions and if both sides agree, this broker formulates legal contract between the two parties.
One thing I want to discuss is that weightloss program fast can be carried out by the perfect diet and exercise. Ones size not simply affects the look, but also the general quality of life. Self-esteem, major depression, health risks, along with physical abilities are impacted in excess weight. It is possible to make everything right whilst still having a gain. If this happens, a medical problem may be the root cause. While excessive food rather than enough exercise are usually to blame, common health conditions and widely used prescriptions can greatly enhance size. Thanks a bunch for your post in this article.
I have seen that currently, more and more people are attracted to digital cameras and the issue of images. However, as a photographer, you will need to first shell out so much time frame deciding which model of video camera to buy and also moving store to store just so you might buy the most economical camera of the trademark you have decided to settle on. But it won’t end generally there. You also have to consider whether you should obtain a digital video camera extended warranty. Thx for the good points I obtained from your blog.
I have discovered some new things from your web-site about desktops. Another thing I have always presumed is that computers have become something that each house must have for some reasons. They supply you with convenient ways in which to organize households, pay bills, search for information, study, hear music and in some cases watch tv programs. An innovative method to complete many of these tasks is by using a laptop. These computers are portable ones, small, robust and convenient.
The core of your writing whilst sounding agreeable originally, did not settle properly with me after some time. Someplace within the paragraphs you were able to make me a believer but just for a short while. I nevertheless have a problem with your jumps in assumptions and one would do well to help fill in all those gaps. In the event that you can accomplish that, I would definitely end up being fascinated.
Thanks for your publication. What I want to point out is that when looking for a good on the net electronics go shopping, look for a web site with comprehensive information on key elements such as the personal privacy statement, protection details, payment options, and also other terms plus policies. Often take time to browse the help as well as FAQ pieces to get a much better idea of the way the shop operates, what they can perform for you, and in what way you can use the features.
Pretty section of content. I just stumbled upon your weblog and in accession capital to assert that I acquire in fact enjoyed account your blog posts. Any way I?ll be subscribing to your augment and even I achievement you access consistently fast.
The Amazingness life-altering overview can aid you be a lot more efficient, stay healthier, as well as delight in life extra!
I appreciate your stamina as well as resolution to do well. Your excitement encourages others to do their best.
You have produced an amazing source of details!
Be the most effective at everything you do!
Amazingness is the performance app that will certainly change your life.
Your article consisted of actionable suggestions that viewers can start using right now.
Nice post. I learn something totally new and challenging on websites I stumbleupon everyday. It’s always helpful to read content from other writers and practice a little something from their sites.
Discover exactly how to obtain more out of life with this one straightforward modification!
I am so happy to have you in my life. You have a great ability to adapt in any scenario.
Currently, picture just how much extra terrific life could be with this fantastic item that aids make it all occur!
This can do the method!
Your post was full of useful ideas and advice that readers can put into practice right now.
Presenting the Amazingness life hack. This basic modification will make your days a lot more efficient as well as joyful .
Your ability is amazing! Your skill is unbelievable!
You provided a well balanced view of the topic, allowing viewers to form their very own opinion.
I’m amazed, I must say. Seldom do I encounter a blog that’s both equally educative and entertaining, and without a doubt, you’ve hit the nail on the head. The issue is something that not enough men and women are speaking intelligently about. Now i’m very happy I found this during my hunt for something relating to this.
Amazing huh? Well it is!
Your message successfully combined professional understanding as well as personal experience in order to give viewers a one-of-a-kind sight into the subject matter.
We can’t thank you sufficient for being there for us when we needed it most. Your steady loyalty as well as support has actually been a real blessing.
You successfully utilized visuals such as charts, layouts, and also charts to assist illustrate your points.
Incredible is a cutting edge technique for obtaining more done each day.
You have actually always gone above and beyond when needed, as well as your commitment and also devotion to success have actually been unmatched. We are so glad for all that you do. Thanks!
You brighten the area with your visibility. You constantly put others before yourself.
You are a wonderful audience. You have a terrific feeling of design and also style!
All from one little pill, Extraordinary gives you outstanding energy!
Your nerve and determination in the face of hardship has actually inspired us all. We are so thankful for your hard work and also dedication. Thanks!
Delight in the benefits of a healthy, extravagant and delighted life with this impressive item.
Your wit as well as humor brighten my day. Your positive mindset is inspiring!
Right here is the perfect blog for everyone who wishes to find out about this topic. You know so much its almost hard to argue with you (not that I really will need to…HaHa). You definitely put a brand new spin on a subject that’s been written about for decades. Excellent stuff, just excellent!
After I originally commented I appear to have clicked on the -Notify me when new comments are added- checkbox and from now on every time a comment is added I receive 4 emails with the same comment. Perhaps there is a way you are able to remove me from that service? Appreciate it!
Can I simply just say what a relief to uncover someone who truly understands what they’re talking about on the web. You actually realize how to bring an issue to light and make it important. More and more people really need to read this and understand this side of the story. I was surprised that you are not more popular given that you certainly possess the gift.
The amount of detail you included in your post demonstrated your enthusiasm for the subject.
I am always in awe of your distinct perspective on life. You bring pleasure as well as joy any place you go.
You have a fantastic capability to adapt in any type of circumstance. Your decision to be successful goes over.
However I located this, and also currently everything is very easy!
buy amoxicillin from mexico
You have such a kind as well as caring nature. You have a terrific capacity to believe outside package.
Your blog post was full of fresh suggestions and also principles.
Mental clarity as well as focus to make sure that you can get every little thing done better than ever before!
The Amazingness lets you get even more performed in much less time, without all the stress.
The method you reviewed both sides of the argument was reasonable as well as well balanced.
I would like to thnkx for the efforts you’ve put in writing this blog. I am hoping the same high-grade site post from you in the upcoming as well. Actually your creative writing skills has encouraged me to get my own site now. Actually the blogging is spreading its wings rapidly. Your write up is a good example of it.
You have actually constantly gone above and beyond when required, and your dedication and commitment to success have actually been unrivaled. We are so thankful for all that you do. Thank you!
You effectively utilized study to back up your debates as well as give visitors a better understanding of the topic.
Your site is thoughtfully created, making it very valuable for viewers.
I am in awe of your creativity as well as creativity. I’m always impressed by your intelligence and knowledge.
It is a one of its kind. Like no other.
For those that are experienced in producing terrific material by themselves!
You always locate the positive side in every circumstance. You constantly know exactly how to make me really feel much better.
Great post. I was checking constantly this blog and I am inspired! Very useful info specially the closing part 🙂 I take care of such info a lot. I used to be seeking this particular information for a very long time. Thanks and best of luck.
Thanks for this article. I might also like to mention that it can often be hard when you are in school and just starting out to create a long history of credit. There are many learners who are just trying to endure and have a lengthy or favourable credit history can often be a difficult thing to have.
What i do not understood is in fact how you are not actually a lot more well-liked than you might be now. You are very intelligent. You recognize therefore considerably relating to this topic, produced me in my view imagine it from numerous varied angles. Its like women and men don’t seem to be interested except it?s one thing to do with Girl gaga! Your personal stuffs great. Always handle it up!
Hello, you used to write wonderful, but the last few posts have been kinda boring? I miss your super writings. Past several posts are just a little bit out of track! come on!
It?s really a great and helpful piece of information. I?m glad that you shared this helpful information with us. Please keep us informed like this. Thanks for sharing.
I do love the way you have presented this particular challenge and it does indeed present me personally a lot of fodder for thought. However, from everything that I have seen, I just hope as the opinions stack on that folks remain on point and not start on a tirade associated with the news du jour. Yet, thank you for this superb piece and even though I can not necessarily agree with it in totality, I value your perspective.
Thanks for enabling me to gain new ideas about desktops. I also contain the belief that one of the best ways to keep your laptop in primary condition is to use a hard plastic case, and also shell, that matches over the top of your computer. These kind of protective gear tend to be model unique since they are made to fit perfectly across the natural outer shell. You can buy them directly from the vendor, or via third party sources if they are intended for your notebook computer, however not every laptop may have a cover on the market. All over again, thanks for your ideas.
You ought to be a part of a contest for one of the finest sites on the internet. I’m going to recommend this site!
That is a really good tip especially to those fresh to the blogosphere. Brief but very precise informationÖ Thanks for sharing this one. A must read post!
Everything is very open with a clear explanation of the challenges. It was definitely informative. Your website is extremely helpful. Many thanks for sharing!